Part 1: Designing a Scalable Cisco Network Topology: Core, Distribution, and Access Layers
In today’s enterprise environments, building a robust, secure, and scalable network is essential to…..
Read Article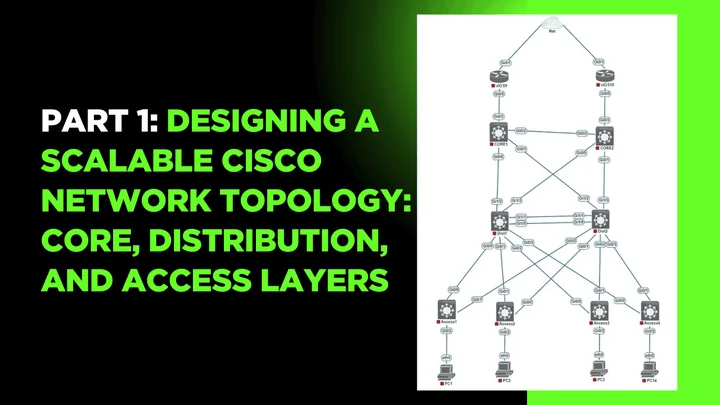
Latest Articles
Insights and stories that capture the essence of contemporary culture.
Editor's Picks
Carefully selected stories that showcase exceptional creativity and insight.

Part 1: Designing a Scalable Cisco Network Topology: Core, Distribution, and Access Layers
In today’s enterprise environments, building a robust, secure, and scalable network is essential to support business operations. Whether it’s handlin….

How to Configure VLANs and Trunk Port on Cisco Switch
A VLAN is a group of devices on one or more LANs that are configured to communicate as if they were attached to the same wire, when in fact they are ….

VLANs, Access and Trunking Ports on Cisco vs JunOS
Both Cisco IOS and Juniper JunOS, the operating systems for their respective networking devices, implement VLANs with similar core functionalities bu….
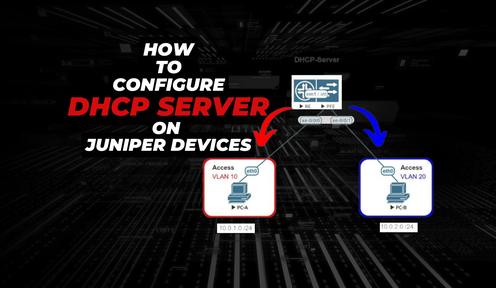
How to Configure DHCP Server on Juniper Router and Switch
Dynamic Host Configuration Protocol (DHCP) is a network protocol that enables a server to automatically assign an IP address to a computer from a def….

How to Configure Console, AUX, Telnet, Enable, and Enable Secret Passwords on a Cisco Router
When setting up a Cisco router, it's essential to configure various passwords to secure different modes and access points. Here are the five main typ….
Subscribe to Our Newsletter
Join our community of readers and receive the latest blogs and insights delivered directly to your inbox.
We respect your privacy. Unsubscribe at any time.